Are you prepared to defend against one of the most pervasive threats in the online world today? Ransomware, a formidable cybersecurity menace, holds files hostage and demands payment, impacting both individuals and organizations at an alarming rate. This comprehensive guide dives into the intricacies of ransomware, from its evolving tactics and the targets in its crosshairs to the critical defensive strategies necessary for protection.
Learn about the sophisticated ways ransomware spreads, the importance of cybersecurity practices such as regular software updates and backups, and how tools like SpyHunter are essential in fortifying your digital defenses. Join us as we explore how to stay one step ahead of ransomware threats and ensure your digital assets remain secure.

What Defines Ransomware in Today’s Threat Landscape?
Ransomware has emerged as one of the most significant cybersecurity threats to both individuals and organizations worldwide. This malicious software, which encrypts files and demands payment for their release, has evolved rapidly, reflecting changes in technology, payment methods, and cybercriminal tactics. Understanding the nature of ransomware, its operation, and its implications is crucial for effective prevention and response.
Ransomware attacks are characterized by their use of encryption to lock access to files, systems, or entire networks. What sets these attacks apart in the current digital environment is their sophisticated exploitation of vulnerabilities, including those in human behavior. Phishing emails, deceitful links, and compromised websites remain common vectors for ransomware dissemination. However, the cybersecurity landscape now also faces more advanced distribution methods, such as exploiting network vulnerabilities and using fileless malware techniques that leave fewer footprints for detection systems to identify.
One of the distinctive aspects of modern ransomware is its ability to leverage cryptocurrencies like Bitcoin for ransom payments. This shift from traditional payment methods to digital currencies has made tracing transactions and identifying perpetrators significantly more challenging. Furthermore, ransomware operators often threaten not just to deny access to data but also to release sensitive information publicly if their demands are not met, adding an element of data breach and reputational damage alongside the direct impact of encryption.
The evolution of ransomware also reflects in the targets it seeks. While initially, individual users were the primary victims, today’s ransomware campaigns increasingly focus on businesses and organizations that can afford larger ransoms. Healthcare institutions, educational entities, government agencies, and large corporations represent valuable targets due to the critical nature of their data and services.
Preventing and mitigating ransomware attacks in this complex landscape requires a multifaceted approach. Users and organizations must adopt robust security practices, including regular software updates, backups, and employee training on recognizing phishing attempts. In addition, implementing advanced threat detection systems and employing comprehensive security solutions like SpyHunter can enhance an organization’s resilience against ransomware. SpyHunter, with its sophisticated scanning algorithms, can identify and remediate ransomware threats, providing an essential layer of defense in a holistic cybersecurity strategy.
Is Your Network Safe? Identifying Vulnerabilities to Ransomware Attacks
In our interconnected world, ensuring network safety against ransomware attacks has become a paramount concern for individuals and businesses alike. Ransomware, a malicious software that encrypts files and demands payment for their release, exploits vulnerabilities within network systems. However, identifying these vulnerabilities before an attacker does can significantly mitigate the risk.
To safeguard your network, it is essential to regularly update and patch software and systems. Outdated programs are a beacon for cybercriminals looking for easy access. Employing a reliable security solution like SpyHunter can offer an additional layer of defense by detecting and removing malware threats that could lead to ransomware infections.
Furthermore, educate your team or family members about the dangers of phishing emails and malicious attachments, as these are common vectors for ransomware. Implementing strong access controls and using multifactor authentication can also prevent unauthorized access to sensitive information.
Finally, back up your data regularly. In the event of a ransomware attack, having backup copies of your important files can be the difference between a quick recovery and a catastrophic loss. This simple step, along with the above measures, can dramatically improve your network’s resilience against ransomware attacks.
The Unseen Risks of Public Wi-Fi Networks
Public Wi-Fi networks, while convenient, present significant risks, especially related to ransomware attacks. These networks are often unsecured, allowing cybercriminals to intercept data transmitted over the network or deploy malware directly to connected devices.
To protect yourself, avoid conducting sensitive transactions, like banking or accessing sensitive work documents, on public Wi-Fi. If public Wi-Fi use is unavoidable, a VPN (Virtual Private Network) can encrypt your internet connection, making it much harder for hackers to access your data. Also, ensure your device’s firewall is enabled and consider using security software, like SpyHunter, which can protect against malware attempting to exploit public Wi-Fi vulnerabilities.
Being cautious about the Wi-Fi networks you connect to and taking preventive measures can significantly reduce the risk of falling victim to ransomware and other cyber threats.
Email Phishing: The Gateway to Ransomware Exploits
Email phishing is one of the most common methods used by attackers to distribute ransomware. Phishing emails are designed to trick you into clicking on a link or downloading an attachment that contains malicious software. It’s critical to recognize and avoid these emails to protect your network from ransomware.
Always verify the sender’s email address for any signs of suspicious activity and avoid opening attachments or clicking links from unknown sources. Educate yourself and your team on the latest phishing tactics, as cybercriminals continuously evolve their techniques to bypass security measures.
Implementing secure email gateways and targeted attack protection can help filter out potentially dangerous emails before they even reach your inbox. Combined with user vigilance and comprehensive security solutions like SpyHunter, you can create a robust defense against the phishing emails that lead to ransomware infections.
Remember, prevention is the key to maintaining the security of your network against the ever-present threat of ransomware. By understanding your vulnerabilities and taking proactive steps to address them, you can significantly decrease the likelihood of a successful ransomware attack.
Here’s an example of a phishing email that distributes ransomware via a malicious link:
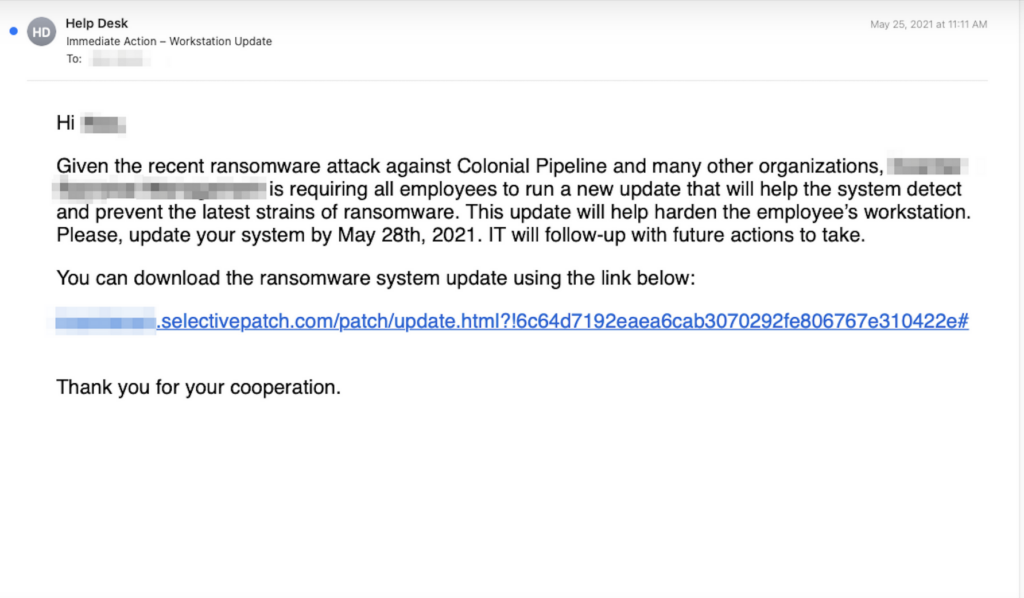
Comprehensive Strategies for Ransomware Prevention
Ransomware attacks can disrupt business operations and result in significant financial losses. Understanding and implementing comprehensive strategies for ransomware prevention is essential for safeguarding your organization’s digital assets. Below, we detail effective measures that bolster your cybersecurity posture, minimizing the risk of ransomware incidents.
Implementing Strong Password Policies
Strong password policies are your first line of defense in securing your systems against unauthorized access. A robust password policy encourages the creation of complex and unique passwords that are hard for attackers to guess. Here are steps to ensure effective password policies:
- Create Complexity Requirements: Mandate a mix of uppercase, lowercase letters, numbers, and special characters for all passwords.
- Implement Regular Changes: Set a schedule for password updates, encouraging users to change their passwords every 90 days.
- Advocate for Length Over Complexity: Encourage passwords that are long and easy to remember rather than complex and written down.
- Use Multi-Factor Authentication (MFA): Adding an extra layer of security, MFA requires a second form of verification beyond just the password, significantly increasing account security.
- Educate Employees: Regular training sessions can help employees understand the importance of strong passwords and secure practices.
In instances where password management becomes a challenge, recommending a trusted password manager, which can generate, store, and auto-fill your passwords, might be beneficial. Remember, keeping your passwords secure is a critical step towards preventing unauthorized access to your systems.
Regular Software Updates: Your First Defense
One of the most straightforward yet frequently overlooked aspects of cybersecurity is keeping your software updated. Regular software updates not only provide new features and improvements but also fix security vulnerabilities that could be exploited by ransomware attacks. Here’s how to make software updates an integral part of your cybersecurity strategy:
- Automate Whenever Possible: Enable automatic updates for your operating system, applications, and any other software where applicable.
- Centralize Patch Management: Use a centralized patch management system to ensure all devices are updated simultaneously and to track compliance across your organization.
- Prioritize Critical Updates: Always prioritize the installation of updates deemed critical or security-related to mitigate the risk of exploitation.
- Regular Vulnerability Assessments: Regularly assess your systems for vulnerabilities to ensure there are no exposed threats that could be exploited.
By ensuring your systems are up-to-date, you significantly reduce the risk of attackers exploiting known vulnerabilities to launch ransomware attacks.
The Importance of Security Awareness Training
Human error is a significant factor in the success of ransomware attacks, making security awareness training an indispensable part of a comprehensive prevention strategy. Here’s how you can conduct effective training:
- Conduct Regular Training Sessions: Provide ongoing training that covers the latest cybersecurity threats, including ransomware, and best practices for preventing them.
- Simulate Phishing Attacks: Use simulated phishing exercises to teach employees how to recognize and respond to malicious emails.
- Encourage Open Communication: Create an environment where employees feel comfortable reporting potential security threats without fear of repercussions.
- Highlight Real-World Scenarios: Use case studies and news articles about recent ransomware attacks to demonstrate the real-world impact of cybersecurity threats.
- Review Policies Regularly: Regularly review and update your cybersecurity policies to reflect the latest threats and security best practices.
Including security awareness as a core element of your organization’s culture can dramatically decrease the likelihood of successful ransomware attacks. Encouraging vigilance and educating your team on how to recognize and respond to threats will fortify your organization’s defenses against ransomware and other cybersecurity threats.
When it comes to protecting your organization from ransomware, utilizing a comprehensive cybersecurity solution like SpyHunter can provide an additional layer of security. SpyHunter’s advanced malware detection and removal capabilities can help identify and eliminate ransomware threats before they can cause harm, ensuring your organization’s digital environment remains secure.
Why SpyHunter Is Your Best Ally Against Ransomware Threats
In today’s ever-evolving threat landscape, where ransomware attacks are becoming increasingly sophisticated and frequent, choosing the right security software is more critical than ever. SpyHunter emerges as a formidable ally in this battle, providing comprehensive protection designed to neutralize ransomware threats before they can cause harm. This multi-layered defense strategy not only prevents ransomware from infiltrating your system but also offers real-time protection to safeguard your digital life.
Real-time Protection Features of SpyHunter
SpyHunter is engineered with advanced real-time protection features that actively monitor and protect your system against ransomware and other malicious threats. These features include:
- Behavioral Analysis: SpyHunter uses sophisticated algorithms to detect patterns and behaviors common to ransomware, allowing it to identify and stop threats that traditional, signature-based methods might miss.
- Heuristic Detection: This approach helps SpyHunter identify new and emerging threats by examining the characteristics of files and applications for suspicious activity, without relying on known virus signatures.
- Continuous Updates: To combat the rapidly evolving nature of ransomware, SpyHunter regularly updates its threat database, ensuring your system is protected against the latest threats.
- Safe Browsing: SpyHunter monitors your internet browsing activities to prevent access to malicious websites that could introduce ransomware into your system.
- Custom Malware Fixes: In the event that ransomware breaches your defenses, SpyHunter offers custom malware fixes, tailored to tackle specific threats detected on your system.
These real-time protection features are part of what makes SpyHunter an essential tool in the fight against ransomware, keeping your system secure and your data protected at all times.
How SpyHunter Helps in Preventing Ransomware Infections
Preventing ransomware infections requires more than just a passive defense; it demands proactive measures that SpyHunter excels in providing. Here’s how SpyHunter helps in avoiding these pervasive threats:
- Email Security: Many ransomware attacks initiate from phishing emails. SpyHunter scans your emails for malicious links and attachments, significantly reducing the risk of a ransomware infection.
- Network Protection: SpyHunter tracks data packets entering and leaving your system, identifying and blocking any ransomware-related communications before they can execute their payload.
- File Guard: This feature ensures that any newly downloaded files are thoroughly scanned for ransomware and other threats before they can cause any damage.
- Exclusion Settings: SpyHunter allows you to exclude certain programs from being scanned, which is helpful for software developers or those who frequently use trusted third-party applications not recognized by generic security programs.
- Ransomware Remediation: Should your system fall victim to a ransomware attack, SpyHunter’s remediation features work to reverse the encryption and damage caused by ransomware, aiming to restore your files and system to their pre-attack state.
By incorporating SpyHunter into your cybersecurity routine, you significantly bolster your defenses against ransomware. Its proactive and comprehensive protection features ensure that your system remains secure, allowing you to navigate the digital environment with confidence and peace of mind.
Step-by-Step Guide on How to Detect and Remove Ransomware
When your device falls victim to ransomware, it’s crucial to recognize the infection early and take prompt action to mitigate the damage. This guide provides a clear roadmap to detect and efficiently remove ransomware from your infected systems.
Identifying the Signs of a Ransomware Infection
Ransomware can be discreet, but it often leaves behind several tell-tale signs that indicate an infection. Some common indicators include:
- Unexpected pop-up messages demanding a ransom payment in exchange for decrypting your files.
- Inability to access your files, which may now have strange extensions that weren’t there before.
- A significant slowdown in system performance, as ransomware can consume considerable system resources.
- Altered desktop wallpaper or screensavers, often replaced by a ransom note or warning message.
- Files that fail to open, displaying messages that your data has been encrypted.
Noticing any of these symptoms should prompt immediate action to confirm the presence of ransomware and begin the removal process to prevent further damage.
Effective Removal of Ransomware: Do’s and Don’ts

Once ransomware is detected, a strategic approach to its removal is essential. Here’s what you should and shouldn’t do:
Do:
- Isolate the Infected Device: Immediately disconnect the affected device from the internet and any network connections to prevent the spread of ransomware to other devices.
- Identify the Ransomware Type: Use resources like the No More Ransom project to determine the ransomware variant you’re dealing with. This information is crucial for finding a potential decryption tool.
- Employ Security Software: Run a reputable security solution like SpyHunter to scan your device thoroughly. SpyHunter can help identify and remove ransomware and any other malware threats present.
- Contact Professionals: Consider getting help from cybersecurity experts, especially when dealing with sophisticated ransomware infections. Professionals can provide advice on the removal process and data recovery.
- Report the Incident: Inform law enforcement agencies about the ransomware attack. They can offer guidance and help prevent future attacks.
Don’t:
- Pay the Ransom: Paying the ransom offers no guarantee that you’ll get your files back and encourages cybercriminals to continue their nefarious activities.
- Continue Using the Infected Device: Using the compromised device can lead to further encryption or data loss. Ensure the device remains isolated until fully cleaned.
- Attempt Manual Clean-up Without Expertise: Unless you’re skilled in cybersecurity, trying to remove ransomware manually can result in irreversible data loss or could exacerbate the issue.
The steps outlined above are designed to assist in the rapid detection and removal of ransomware. By following a methodical approach and utilizing SpyHunter for malware detection and removal, you can enhance your chances of recovering from an infection with minimal damage. Remember, the best defense against ransomware is proactive prevention, including regular backups, up-to-date security patches, and a robust cybersecurity solution.
Developing a Powerful Data Backup Strategy
Crafting a data backup strategy is crucial for safeguarding your important documents, photos, and files from unexpected events like cyberattacks or hardware failure. A well-thought-out strategy involves choosing the right mix of backup solutions, scheduling regular backups, and testing the backups to ensure data can be restored when needed. It’s not just about having copies of your data; it’s about making those copies in a way that aligns with your needs while ensuring they remain secure and accessible.
Cloud vs. Local Backups: Pros and Cons
Choosing between cloud and local backups is a foundational decision in developing your backup strategy. Both options have their unique advantages and limitations, which should be considered carefully to meet your backup needs effectively.
- Cloud Backups: Cloud backups store your data on remote servers accessible from anywhere with an internet connection. This off-site feature is beneficial for recovery in case of physical disasters. Cloud services often provide scalable storage options and built-in security measures. However, reliance on an internet connection and ongoing subscription costs are potential drawbacks.
- Local Backups: Local backups involve storing data on external hard drives, USB sticks, or network-attached storage systems physically located at your premises. They offer fast recovery times and a one-time cost for the storage device. Yet, they’re vulnerable to physical damage (e.g., fire, theft) and might not offer the same level of encryption and security measures as cloud-based solutions.
In many cases, a combination of both cloud and local backups will provide the most comprehensive protection, taking advantage of the strengths of each method while mitigating the other’s weaknesses.
How Often Should You Backup Your Data?
The frequency of backups should match the importance of your data and how often it changes. Regular backups minimize the risk of significant data loss in between backups, making it easier to recover up-to-date information following a data loss event.
- Daily Backups: Essential for data that changes daily, ensuring minimal work is lost in case of a computer failure or ransomware attack. This frequency is often recommended for businesses or for individuals who work with critical data regularly.
- Weekly or Monthly Backups: Suitable for data that does not change as frequently or for personal files that are not updated often. Choosing between weekly or monthly backups often depends on how devastating a potential loss of a month’s worth of data would be.
Automating your backup process can help adhere to your backup schedule without having to remember to initiate each backup manually. For critical systems and sensitive data, employing a strategy that incorporates incremental backups – backing up only the data that has changed since the last backup – can save storage space and reduce the time each backup takes.
Finally, every backup strategy should include regular tests of the backup copies. Testing ensures that your backups not only exist but are also reliable and can be restored when necessary. It’s also wise to maintain multiple generations of backups, such as weekly, monthly, and yearly archives, depending on the value and lifecycle of your information.
When considering backup solutions, especially software, ensure security and reliability are at the forefront. In contexts where mentioning security or utility software is relevant, such as protecting your backups from ransomware, SpyHunter stands out as an effective solution. Its capabilities in identifying and neutralizing threats can be an invaluable part of safeguarding your backup environment.
Dealing with a Ransomware Attack: Immediate Actions to Take
Facing a ransomware attack can be a stressful situation for any individual or organization. The immediate response can significantly impact the outcome and the speed at which normal operations can resume. When under attack, the first step is to ensure the safety of your remaining digital environment. Isolate the infected systems to prevent the spread of ransomware to connected networks and devices. This action includes disconnecting from the internet, disabling wireless connections like Wi-Fi and Bluetooth, and segregating the affected devices from the rest of your network.
Next, it’s crucial to identify the extent of the attack. Assess which files have been encrypted and determine the ransomware variant to better understand the threat. This evaluation will guide your next steps, including deciding on the feasibility of decryption and the potential for restoring from backups. During this chaotic time, maintaining a clear head and following a structured approach to the situation is essential.
Communication also plays a pivotal role. Inform all stakeholders about the breach to ensure they are aware and prepared to assist in the recovery process. This includes employees, customers, and partners who might be indirectly affected by the attack. Transparency is critical to maintaining trust during and after the recovery process.
Contacting Authorities: When and Why It’s Necessary
One critical step in the wake of a ransomware attack that often gets overlooked is contacting the authorities. Law enforcement agencies like the FBI, CISA or local cybercrime units have the expertise and resources to potentially assist in the recovery process. Reporting the crime can also help in broader efforts to combat the ransomware epidemic by providing authorities with valuable information needed to track down and prosecute cybercriminals. Moreover, in certain jurisdictions, reporting such incidents may be a legal requirement, especially when personal data is breached.
Contacting authorities not only aids in the immediate response but also contributes to the larger fight against digital crime. In addition, law enforcement may offer guidance or resources that can assist in recovery efforts, including advice on whether paying the ransom may lead to recovery or simply fund further criminal activities.
Deciding Whether to Pay the Ransom: A Critical Analysis
The decision to pay a ransom in the event of a ransomware attack is complex and fraught with ethical and practical considerations. On one hand, paying the ransom may seem like the quickest way to regain access to encrypted files. However, compliance with the attackers’ demands does not guarantee the return of data and can also fund future criminal activities, encouraging perpetrators to continue their operations.
Most cybersecurity experts and law enforcement agencies advise against paying the ransom. Instead, they recommend focusing on other recovery strategies, such and seeking out decryption tools provided by security researchers or relying on backups to restore the lost data. It’s also worthwhile to engage with cybersecurity professionals who can assist in assessing the situation and exploring viable recovery options. In cases where critical data is at stake with no backups available, the decision becomes significantly harder and must be made on a case-by-case basis, considering all potential risks and benefits.
During these trying times, preventative measures are invaluable. Organizations should invest in comprehensive cybersecurity solutions like SpyHunter to protect against malware infections including ransomware. Regular backups, employee training on phishing and other common attack vectors, and a robust security policy can significantly mitigate the risk of a ransomware attack and its impacts on the organization.
In summary, when dealing with ransomware, the focus should be on prevention, preparation, and a thoughtful, informed response to attacks. Engaging with law enforcement and cybersecurity experts can provide guidance and support, helping to navigate the aftermath of an attack and to reinforce defenses against future threats.
Future-Proofing Your Organization Against Ransomware
As we approach 2025, it’s clear that ransomware remains a formidable threat to organizations worldwide. The constantly evolving nature of cyber threats necessitates a proactive stance towards cybersecurity. Future-proofing your organization against ransomware involves developing a resilient infrastructure that can withstand attacks without capitulating to the demands of cybercriminals. A comprehensive strategy that includes regular data backups, employee training, and the implementation of advanced threat detection technologies is vital. Incorporating encryption protocols and securing endpoints can significantly mitigate the risk posed by ransomware. In addition, establishing a clear incident response plan ensures that your organization can swiftly respond to and recover from a ransomware attack, minimizing potential damage.
Emerging Ransomware Trends to Watch in 2024 and Beyond
In the coming years, ransomware attacks are expected to become more sophisticated, with cybercriminals targeting not just computers but also Internet of Things (IoT) devices, mobile platforms, and cloud storage. AI-driven ransomware could potentially harness machine learning to evade detection and optimize their spread. Furthermore, the rise of Ransomware-as-a-Service (RaaS) platforms enables even technically inexperienced actors to launch devastating attacks. Awareness of these trends is crucial for cybersecurity strategists seeking to bolster their defenses and prepare for future threats.
To protect against these emerging threats, organizations should prioritize the following:
- Continuous monitoring and updates of all systems to patch vulnerabilities promptly
- Enhanced training programs that educate staff on the latest ransomware tactics and phishing schemes
- Deployment of AI and machine learning-based security solutions to detect and block sophisticated threats
Engaging in active threat intelligence sharing with other organizations and law enforcement can also provide early warnings of new ransomware threats.
Innovations in Cybersecurity: Staying Ahead of Hackers
The cybersecurity industry is rapidly advancing, with new technologies emerging to address the sophisticated tactics employed by cybercriminals. One such innovation is the development of machine learning algorithms that can predict and identify ransomware patterns earlier than traditional methods. Behavioral analysis tools are becoming more fine-tuned, offering the ability to distinguish between legitimate user actions and potentially malicious behaviors indicative of a ransomware attack. Another promising development is blockchain technology for securing transactions and preventing data tampering, offering a new level of integrity assurance in digital interactions.
For individuals and organizations alike, adopting layered security strategies that leverage these technological advancements is crucial. Strategies may include:
- Employing next-generation firewalls and intrusion prevention systems that adapt to new threats
- Using endpoint protection platforms that integrate AI to better detect ransomware
- Implementing secure access service edge (SASE) models for more robust network security
Organizations can significantly enhance their resilience against ransomware by staying informed about cybersecurity innovations and incorporating these technologies into their defense mechanisms. Moreover, in scenarios where the threat landscape evolves beyond the current security measures, tools like SpyHunter can provide an added layer of protection by detecting and removing ransomware and other malware threats efficiently, ensuring the security of sensitive data and assets.
Ransomware Protection and Mitigation: Checklist for 2024
As we move through 2024, the threat landscape continues to evolve, making it more important than ever to adopt robust strategies for ransomware protection and mitigation. This comprehensive checklist is designed to help individuals and organizations bolster their defenses and ensure their digital assets remain secure. By following these straightforward steps, you can significantly reduce the risk of falling victim to a ransomware attack.
- Restrict Access: Limit access to your data and systems to only those who absolutely need it. Implementing strong passwords and multi-factor authentication can add an additional layer of security, making it harder for attackers to gain unauthorized access.
- Centralize Management: Utilize centralized management for your digital assets. This involves categorizing and securing sensitive information effectively, regardless of where it is stored. It’s crucial to have a clear overview of all your data and the protection measures in place.
- Deploy Anti-Malware Solutions: Protecting against ransomware requires proactive measures. Use advanced anti-malware solutions that can block suspicious files, monitor email traffic for malicious content, and identify phishing attacks. For enhanced security, opt for solutions that offer signatureless behavioral analysis to detect and mitigate unknown threats.
- Implement Patch Management: Keep all software and systems up to date with the latest patches. This applies to operating systems, applications, and any connected devices. Timely updates can fix vulnerabilities that ransomware could exploit.
- Secure Backups: Adhering to the 3-2-1 backup rule – keeping three copies of data on two different media, with one stored offsite – is fundamental. Regularly testing backups ensures they are reliable and untampered with, providing a failsafe in the event of an attack.
- Educate Your Team: Awareness is key to prevention. Train employees on the dangers of ransomware, the importance of reporting suspicious activities, and the best practices for maintaining cybersecurity hygiene. Regular updates and training sessions can fortify your first line of defense: your users.
- Prepare for the Worst: Even with strong preventative measures, it’s possible to fall victim to ransomware. Developing and maintaining an incident response and disaster recovery plan ensures you can quickly respond to and recover from such incidents.
- Conduct Risk Assessments: Regularly evaluate your cybersecurity posture to identify vulnerabilities and potential ransomware entry points. This proactive approach allows you to address weaknesses before they can be exploited.
- Create an Incident Response Plan: A clear, concise plan outlining the steps to take in the event of a ransomware attack is crucial. This should include isolating affected systems, identifying the ransomware strain, and knowing when and how to contact authorities.
At the core of these steps, adopting a dedicated anti-ransomware solution like SpyHunter can provide comprehensive protection against a wide range of ransomware attacks. With its advanced threat detection and removal capabilities, SpyHunter is designed to secure your digital environment against the latest ransomware threats.
In summary, protecting against ransomware will require a blend of technological solutions, user education, and preparedness planning. By following this checklist, you can significantly reduce your risk and ensure that, even in the face of an attack, the integrity of your data remains intact. Remember, in the digital age, being proactive is not just an option – it’s a necessity.
A Unified Approach to Ransomware Resistance
Ransomware attacks have rapidly become one of the most formidable threats to digital security, eclipsing many traditional forms of cybercrime. With attackers constantly refining their tactics, individuals and organizations alike find themselves in an ongoing battle to safeguard their digital environments. The key to mounting a successful defense lies in adopting a comprehensive, multilayered strategy that addresses the different stages of potential ransomware infiltration.
At its core, effective ransomware protection involves a blend of proactive measures, timely detection, and robust recovery plans. This unified approach not only helps in thwarting attacks but also ensures minimal disruption and loss in the unfortunate event of a breach. Below, we outline the essentials of building a resilient defense against ransomware.
1. Education and Awareness
Understanding the threat landscape is the first step towards formulating a defense. Educating yourself and your team about how ransomware works, its common delivery methods, and the latest trends in ransomware tactics, helps in fostering a culture of cybersecurity awareness. Regular training sessions can significantly reduce the likelihood of successful phishing attacks, one of the primary vectors for ransomware.
2. Implement Adequate Security Measures
Strong security practices form the foundation of ransomware resistance. This includes the implementation of advanced malware protection tools, rigorous authentication protocols, and comprehensive network security solutions. A dedicated anti-ransomware product, especially one like SpyHunter, can significantly bolster your defenses by offering specialized detection and removal capabilities against ransomware and other malware.
3. Regular Backups and Data Encryption
Securing your data against unauthorized access and ensuring its availability even in the wake of an attack is paramount. Regularly backing up critical data and encrypting sensitive information can prevent significant loss and downtime. Solutions like SafeMode Snapshots offer a streamlined way to protect and recover data, enabling businesses to resume operations swiftly after an attack.
4. Early Detection and Response
Speed is of the essence in identifying and mitigating ransomware threats. Employing tools that monitor your digital ecosystem for suspicious activity can enable you to detect ransomware attacks in their incipient stages. Coupled with an effective incident response plan, these measures ensure you can act swiftly to isolate affected systems, mitigate damage, and prevent the spread of ransomware.
5. Keep Software and Systems Updated
Many ransomware attacks exploit vulnerabilities in outdated software and systems. Regularly updating your operating systems, applications, and security tools with the latest patches is a critical deterrent against such exploits. Ensuring your digital infrastructure is up-to-date reduces the avenues through which ransomware can infiltrate your network.
6. Leverage Operating System and Application Protections
Modern operating systems and applications often come with built-in security features designed to thwart ransomware attacks. For example, Windows 10 includes ransomware protection features that, when activated, provide an additional layer of security. Familiarizing yourself with these built-in tools and integrating them into your overall security framework can provide significant advantages in ransomware resistance.
Conclusion
Combating ransomware requires a proactive and informed approach. The importance of utilizing advanced security software cannot be overstated in our increasingly digital age. Tools like SpyHunter offer comprehensive protection against the myriad forms of malware threatening our online safety. Equally critical to a strong defense against ransomware is the practice of regularly creating backups. By maintaining current backups of important files, you safeguard your data, ensuring that you have a reliable fallback option should you ever fall prey to an attack.
In the unfortunate event that ransomware does compromise your system, it’s essential to know how to respond effectively. First, avoid paying the ransom, as this does not guarantee the return of your files and only encourages criminal activity. Instead, focus on removing the malicious software from your computer. Initiating a deep scan with a trusted security tool like SpyHunter can help identify and eliminate the ransomware. Also, consulting professional advice or seeking support from anti-ransomware communities online can provide further assistance in recovery and prevention.
Finally, educating yourself and staying informed about the latest ransomware tactics and protection strategies is invaluable. Awareness and preparedness are key components in minimizing the risk and impact of these threats. For more detailed guidance on securing your system against ransomware, including real-world protection tests of various security products, exploring reputable sources can offer insights and recommendations tailored to your needs.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for Ransomware with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall Ransomware and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by Ransomware on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Ransomware there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove Ransomware





Step 5: Try to Restore Files Encrypted by Ransomware.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
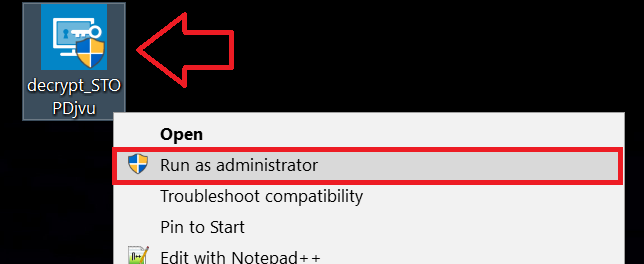
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
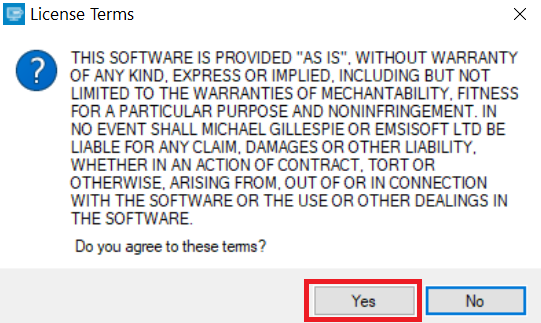
2. Agree with the license terms:
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
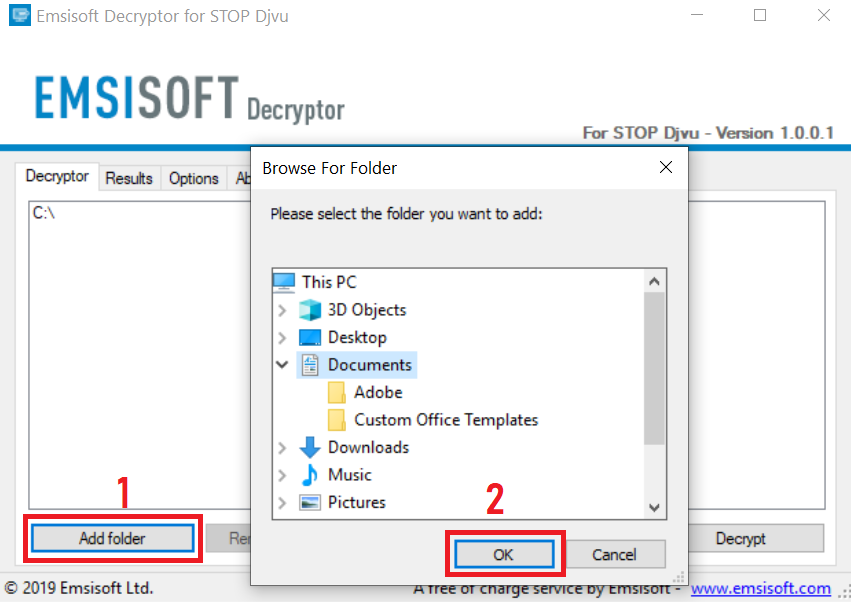
4. Click on "Decrypt" and wait for your files to be decoded.
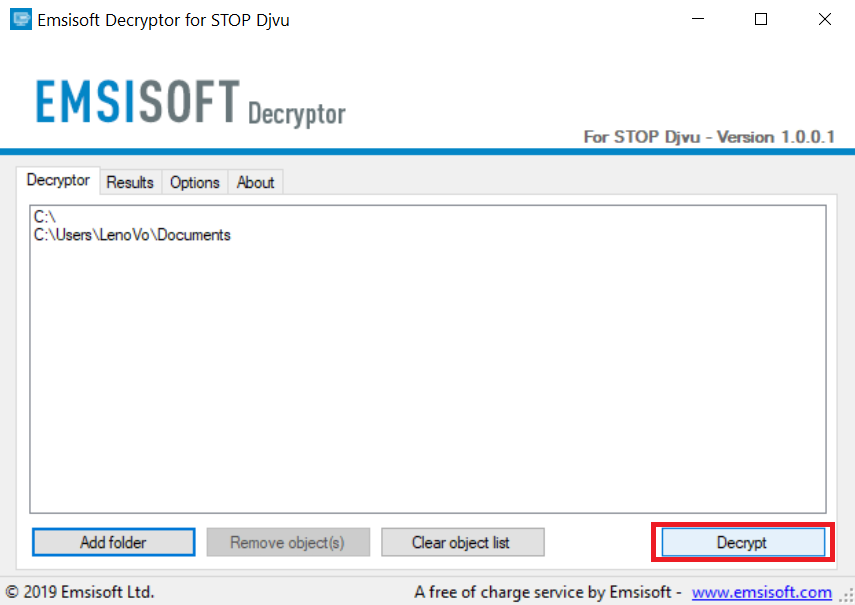
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and Ransomware aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
Ransomware-FAQ
What is Ransomware Ransomware?
Ransomware is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does Ransomware Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does Ransomware Infect?
Via several ways.Ransomware Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of Ransomware is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .Ransomware files?
You can't without a decryptor. At this point, the .Ransomware files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .Ransomware files successfully, then do not despair, because this virus is still new.
Can I Restore ".Ransomware" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .Ransomware files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of Ransomware Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate Ransomware ransomware and then remove it without causing any additional harm to your important .Ransomware files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can Ransomware Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the Ransomware Research
The content we publish on SensorsTechForum.com, this Ransomware how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the Ransomware ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.













